Penetration Test

Executive Summary
A penetration test is a simulated cyberattack that helps organizations identify vulnerabilities in their systems and networks. By simulating real-world attacks, penetration tests can help organizations improve their security posture and reduce the risk of a successful cyberattack.
Introduction
In today’s digital world, it is more important than ever for organizations to protect their systems and networks from cyberattacks. Penetration testing is a valuable tool that can help organizations identify vulnerabilities and improve their security posture.
FAQs
What is the purpose of a penetration test?
A penetration test is a simulated cyberattack that helps organizations identify vulnerabilities in their systems and networks.
Who should conduct a penetration test?
Penetration tests should be conducted by a qualified security professional.
How often should a penetration test be conducted?
The frequency of penetration tests will vary depending on the organization’s needs. However, it is generally recommended that penetration tests be conducted at least once per year.
Top 5 Subtopics
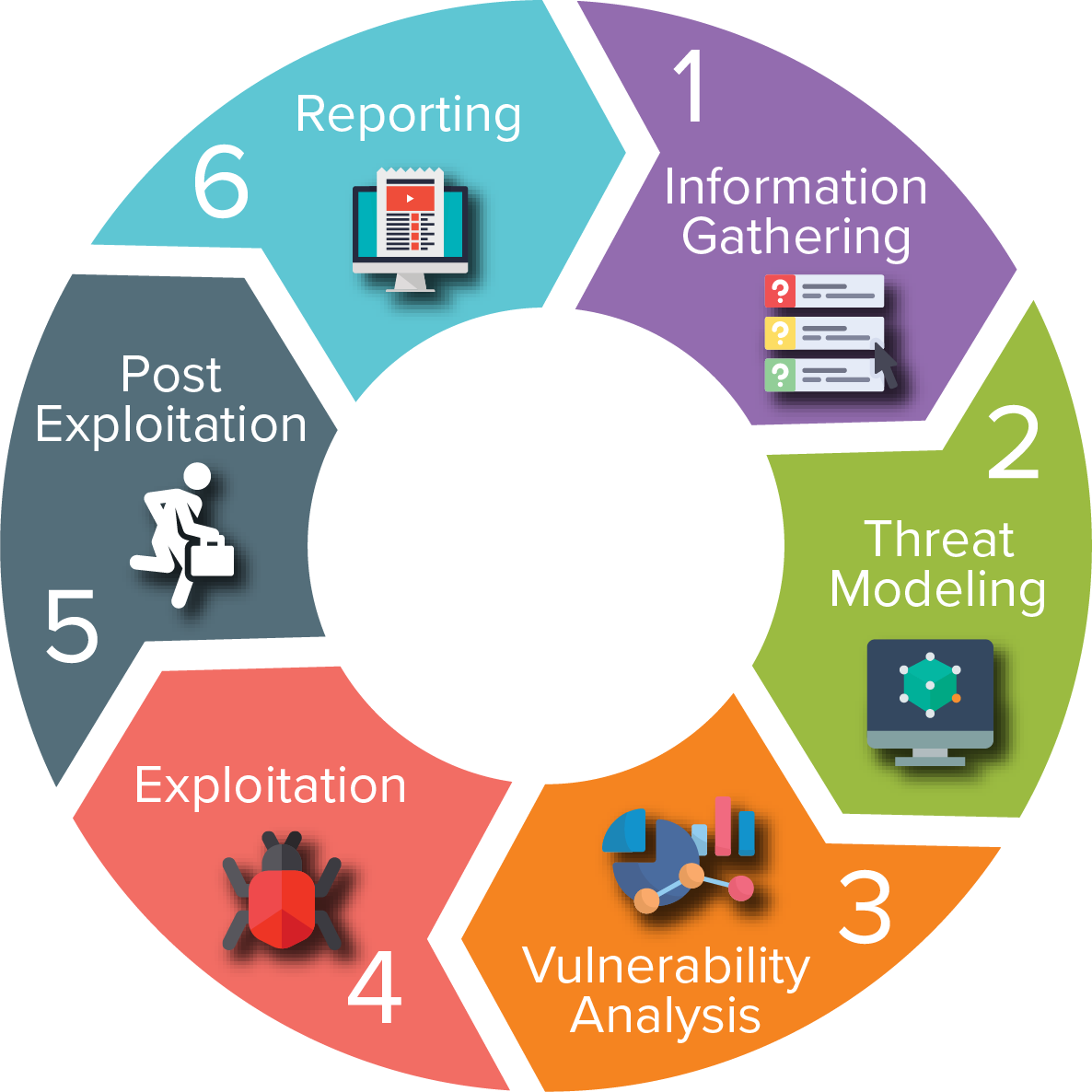
Vulnerability Assessment
A vulnerability assessment is the first step in a penetration test. It involves identifying all of the potential vulnerabilities in a system or network.
- Types of vulnerabilities: There are many different types of vulnerabilities, including software vulnerabilities, hardware vulnerabilities, and network vulnerabilities.
- Vulnerability scanning: Vulnerability scanning is a process of using automated tools to identify vulnerabilities in a system or network.
- Manual vulnerability testing: Manual vulnerability testing is a process of manually testing for vulnerabilities in a system or network.
Attack Simulation
Attack simulation is the second step in a penetration test. It involves simulating real-world attacks to test the effectiveness of an organization’s security controls.
- Types of attack simulations: There are many different types of attack simulations, including network attacks, application attacks, and social engineering attacks.
- Attack vectors: Attack vectors are the different methods that attackers can use to exploit vulnerabilities.
- Attack tools: There are many different attack tools that attackers can use to exploit vulnerabilities.
Risk Assessment
Risk assessment is the third step in a penetration test. It involves evaluating the risk of each vulnerability and developing recommendations for mitigating the risk.
- Risk assessment methodologies: There are many different risk assessment methodologies, each with its own strengths and weaknesses.
- Risk scoring: Risk scoring is a process of assigning a numerical value to each risk.
- Mitigation strategies: Mitigation strategies are actions that can be taken to reduce the risk of a vulnerability being exploited.
Reporting and Remediation
Reporting and remediation are the final steps in a penetration test. The reporting phase involves documenting the findings of the penetration test and making recommendations for mitigating the risks. The remediation phase involves implementing the recommendations and testing the effectiveness of the mitigation measures.
- Reporting formats: There are many different reporting formats, each with its own advantages and disadvantages.
- Remediation plans: A remediation plan is a document that outlines the steps that will be taken to mitigate the risks identified in the penetration test.
- Retesting: Retesting is the process of testing the effectiveness of the mitigation measures.
Continuous Monitoring
Continuous monitoring is an ongoing process of monitoring a system or network for new vulnerabilities. It is important to continuously monitor for new vulnerabilities because attackers are constantly developing new ways to exploit vulnerabilities.
- Monitoring tools: There are many different monitoring tools that can be used to monitor for new vulnerabilities.
- Monitoring techniques: There are many different monitoring techniques that can be used to monitor for new vulnerabilities.
- Security best practices: Security best practices can help to reduce the risk of a successful cyberattack.
Conclusion
Penetration testing is a valuable tool that can help organizations identify vulnerabilities and improve their security posture. By simulating real-world attacks, penetration tests can help organizations identify weaknesses in their systems and networks before attackers can exploit them.
Keywords
- Penetration testing
- Vulnerability assessment
- Attack simulation
- Risk assessment
- Continuous monitoring
