Vulnerability Test Hong Kong

When it comes to protecting your business from cyber threats, knowing where your potential vulnerabilities lie is essential. This can be achieved through a vulnerability test in Hong Kong.
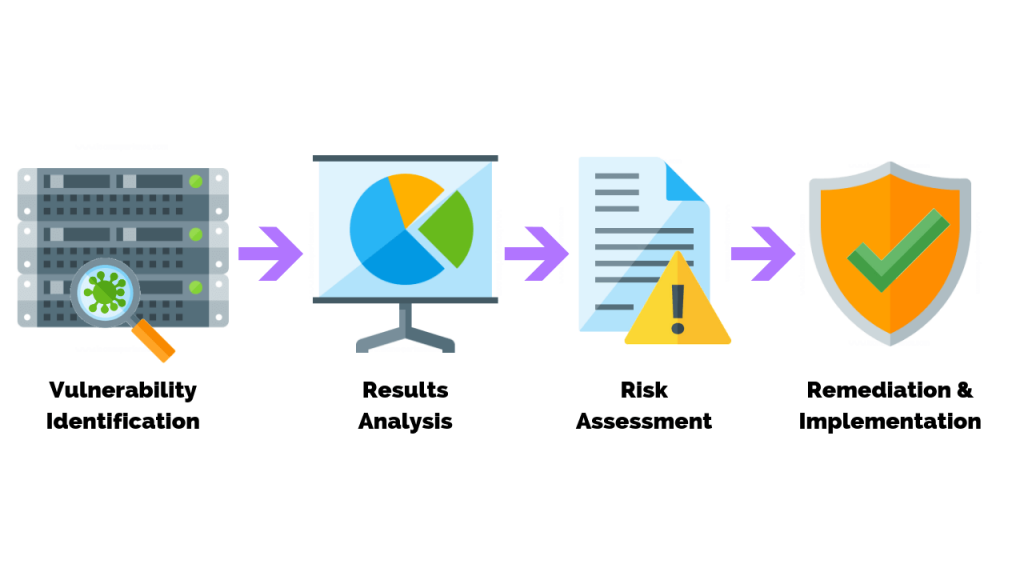
A vulnerability test is a comprehensive assessment of your IT systems, networks, and applications to identify any weaknesses that could be exploited by attackers. It simulates real-world attack scenarios to identify and measure potential threats.
Conducting vulnerability test in Hong Kong offers several benefits for businesses:
- Identifying security gaps and weaknesses before they can be taken advantage of by malicious actors.
- Prioritizing remediation efforts based on the severity of identified vulnerabilities.
- Ensuring compliance with industry standards and regulations that require regular security testing.
- Enhancing the overall security posture of the organization and reducing the risk of cyber attacks.
At [Company Name], we offer comprehensive vulnerability testing services in Hong Kong tailored to meet the specific needs of businesses. Our team of experienced security professionals utilizes industry-leading tools and techniques to thoroughly assess your IT infrastructure for vulnerabilities.
We provide detailed and actionable reports that highlight identified vulnerabilities, assess their severity, and recommend appropriate remediation measures. Our experts collaborate with you to prioritize and address the most critical vulnerabilities, ensuring the ongoing protection of your IT systems.
Schedule a vulnerability test in Hong Kong with [Company Name] today to proactively identify and mitigate potential security risks, safeguard your sensitive data, and protect your business from cyber threats.## Vulnerability Test Hong Kong
Vulnerability testing is a critical component of any comprehensive cybersecurity strategy. By identifying and exploiting vulnerabilities in your systems, you can take steps to mitigate the risk of a cyberattack.
Hong Kong is a global financial center and a major hub for international trade. As such, it is a prime target for cybercriminals. In recent years, there have been a number of high-profile cyberattacks in Hong Kong, including the 2024 Cathay Pacific data breach and the 2024 Hong Kong Stock Exchange hack.
These attacks highlight the importance of vulnerability testing for businesses in Hong Kong. By proactively identifying and addressing vulnerabilities, businesses can protect themselves from the financial and reputational damage that can result from a cyberattack.
Executive Summary
Vulnerability testing is a process of identifying and exploiting vulnerabilities in a computer system. The goal of vulnerability testing is to assess the security of a system and identify any weaknesses that could be exploited by an attacker.
There are a number of different types of vulnerability tests, including:
- Network vulnerability tests assess the security of a network by looking for vulnerabilities in network devices, such as routers and firewalls.
- Web application vulnerability tests assess the security of web applications by looking for vulnerabilities in the code that makes up the application.
- Database vulnerability tests assess the security of databases by looking for vulnerabilities in the database software or configuration.
- Cloud vulnerability tests assess the security of cloud computing environments by looking for vulnerabilities in the cloud provider’s infrastructure or services.
Vulnerability testing is an important part of any comprehensive cybersecurity strategy. By identifying and addressing vulnerabilities, businesses can protect themselves from the financial and reputational damage that can result from a cyberattack.
Introduction
Vulnerability testing is a critical component of any comprehensive cybersecurity strategy. By identifying and exploiting vulnerabilities in your systems, you can take steps to mitigate the risk of a cyberattack.
There are a number of different types of vulnerability tests, each with its own benefits and drawbacks. The type of test that is right for you will depend on your specific needs and goals.
FAQs
What are the benefits of vulnerability testing?
Vulnerability testing can provide a number of benefits, including:
- Identifying vulnerabilities before they can be exploited by attackers
- Prioritizing vulnerabilities based on their risk
- Developing mitigation strategies to address vulnerabilities
- Improving your overall security posture
How often should I perform vulnerability tests?
The frequency of vulnerability testing will depend on a number of factors, including the size and complexity of your network, the frequency of changes to your systems, and the regulatory requirements that you are subject to. However, it is generally recommended to perform vulnerability tests at least once per quarter.
How much does vulnerability testing cost?
The cost of vulnerability testing will vary depending on the size and complexity of your network, the type of test that you need, and the vendor that you choose. However, you can expect to pay anywhere from a few hundred dollars to several thousand dollars for a vulnerability test.
Top 5 Subtopics
Network Security
This subtopic covers the identification and exploitation of vulnerabilities in network devices, such as routers and firewalls. This type of test can help you to identify vulnerabilities that could allow attackers to gain access to your network or to intercept sensitive data.
Web Application Security
This subtopic covers the identification and exploitation of vulnerabilities in web applications. This type of test can help you to identify vulnerabilities that could allow attackers to take control of your web application or to access sensitive data.
Database Security
This subtopic covers the identification and exploitation of vulnerabilities in databases. This type of test can help you to identify vulnerabilities that could allow attackers to access sensitive data or to disrupt the operation of your database.
Cloud Security
This subtopic covers the identification and exploitation of vulnerabilities in cloud computing environments. This type of test can help you to identify vulnerabilities that could allow attackers to gain access to your cloud resources or to disrupt the operation of your cloud services.
Vulnerability Management
This subtopic covers the process of identifying, prioritizing, and mitigating vulnerabilities. This includes developing a vulnerability management plan, implementing vulnerability scanning tools, and patching vulnerabilities.
Conclusion
Vulnerability testing is a critical component of any comprehensive cybersecurity strategy. By identifying and addressing vulnerabilities, businesses can protect themselves from the financial and reputational damage that can result from a cyberattack.
There are a number of different types of vulnerability tests, each with its own benefits and drawbacks. The type of test that is right for you will depend on your specific needs and goals.
If you are not sure how to perform vulnerability tests, there are a number of resources available to help you. You can find online tutorials, training courses, and even professional services that can help you to get started.
Keyword Tags
- Vulnerability Test
- Network Security
- Web Application Security
- Database Security
- Cloud Security
