Vulnerability Test Malaysia
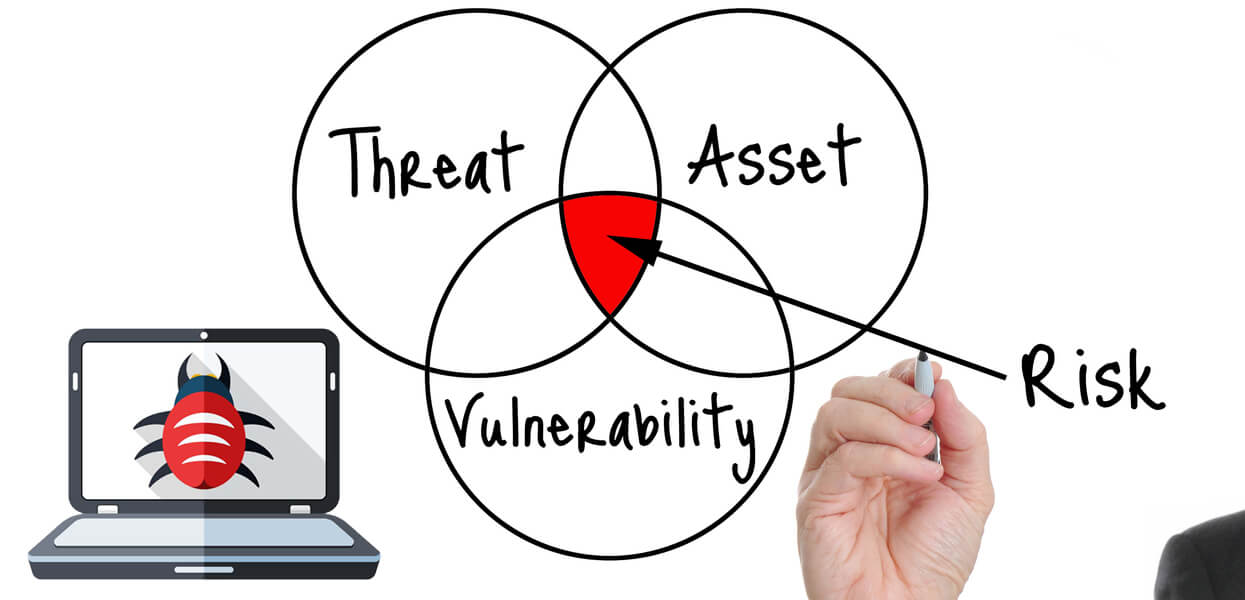
Overview

Vulnerability testing is a type of security assessment that identifies, quantifies, and prioritizes vulnerabilities in a computer system, network, or application. It is a crucial step in the process of securing information systems and protecting against cyber threats.
Importance of Vulnerability Testing
Vulnerability testing is important for several reasons:
- Identifies Security Weaknesses: It helps identify security weaknesses that could be exploited by attackers, allowing organizations to take steps to mitigate them.
- Compliance with Regulations: Many industries and regulations require organizations to conduct vulnerability testing to demonstrate compliance with security standards.
- Reduces Risk of Cyber Attacks: By identifying vulnerabilities, organizations can proactively address them, reducing the likelihood and impact of cyber attacks.
- Enhances Security Posture: Vulnerability testing provides organizations with a comprehensive understanding of their security posture, enabling them to make informed decisions for strengthening their defenses.
Types of Vulnerability Tests
There are several types of vulnerability tests that can be performed, including:
- Network Scans: Scan external and internal networks to identify open ports, services, and network vulnerabilities.
- Application Scans: Scan web applications, mobile applications, and other software to identify security flaws and potential entry points for attackers.
- Intrusion Tests: Simulate real-world attacks to test the effectiveness of security defenses and identify potential vulnerabilities.
- Social Engineering Assessments: Evaluate the susceptibility of employees to social engineering attacks, such as phishing and spear-phishing.
Benefits of Vulnerability Testing in Malaysia
Vulnerability testing offers several benefits for organizations in Malaysia:
- Compliance with Industry Regulations: Malaysian organizations operating in certain industries, such as banking, healthcare, and government, are required to conduct vulnerability testing as part of their compliance with regulatory frameworks.
- Protection of Critical Infrastructure: Malaysia’s critical infrastructure, including energy, water, and transportation systems, heavily relies on information technology. Vulnerability testing helps identify and mitigate security weaknesses that could affect these vital services.
- Enhanced Cyber Security Preparedness: With the increasing prevalence of cyber threats, vulnerability testing allows organizations to improve their cybersecurity posture and prepare for potential attacks.
- Competitive Advantage: Organizations that demonstrate strong security practices through vulnerability testing can gain a competitive advantage in attracting customers and investors.
Conclusion
Vulnerability testing is a vital component of any cybersecurity strategy and is essential for organizations in Malaysia to protect their systems and data from cyber attacks. By identifying and mitigating vulnerabilities, organizations can enhance their security posture, comply with regulations, and create a more secure environment for their customers and stakeholders.## Vulnerability Test Malaysia
Executive Summary
Vulnerability testing is a critical part of any cybersecurity strategy. It helps organizations identify and remediate vulnerabilities in their systems before they can be exploited by attackers. In Malaysia, there are several leading providers of vulnerability testing services. These providers offer a range of services, from basic vulnerability scans to comprehensive penetration testing.
Introduction
Vulnerability testing is the process of identifying and assessing vulnerabilities in a computer system. Vulnerabilities can be software flaws, misconfigurations, or weaknesses in network security. Attackers can exploit vulnerabilities to gain unauthorized access to a system, steal data, or disrupt operations.
FAQs
- What is vulnerability testing?
Vulnerability testing is the process of identifying and assessing vulnerabilities in a computer system.
- Why is vulnerability testing important?
Vulnerability testing is important because it helps organizations identify and remediate vulnerabilities before they can be exploited by attackers.
- How often should I conduct vulnerability testing?
The frequency of vulnerability testing depends on the size and complexity of your organization’s network. However, it is generally recommended to conduct vulnerability testing at least once per year.
Top 5 Subtopics
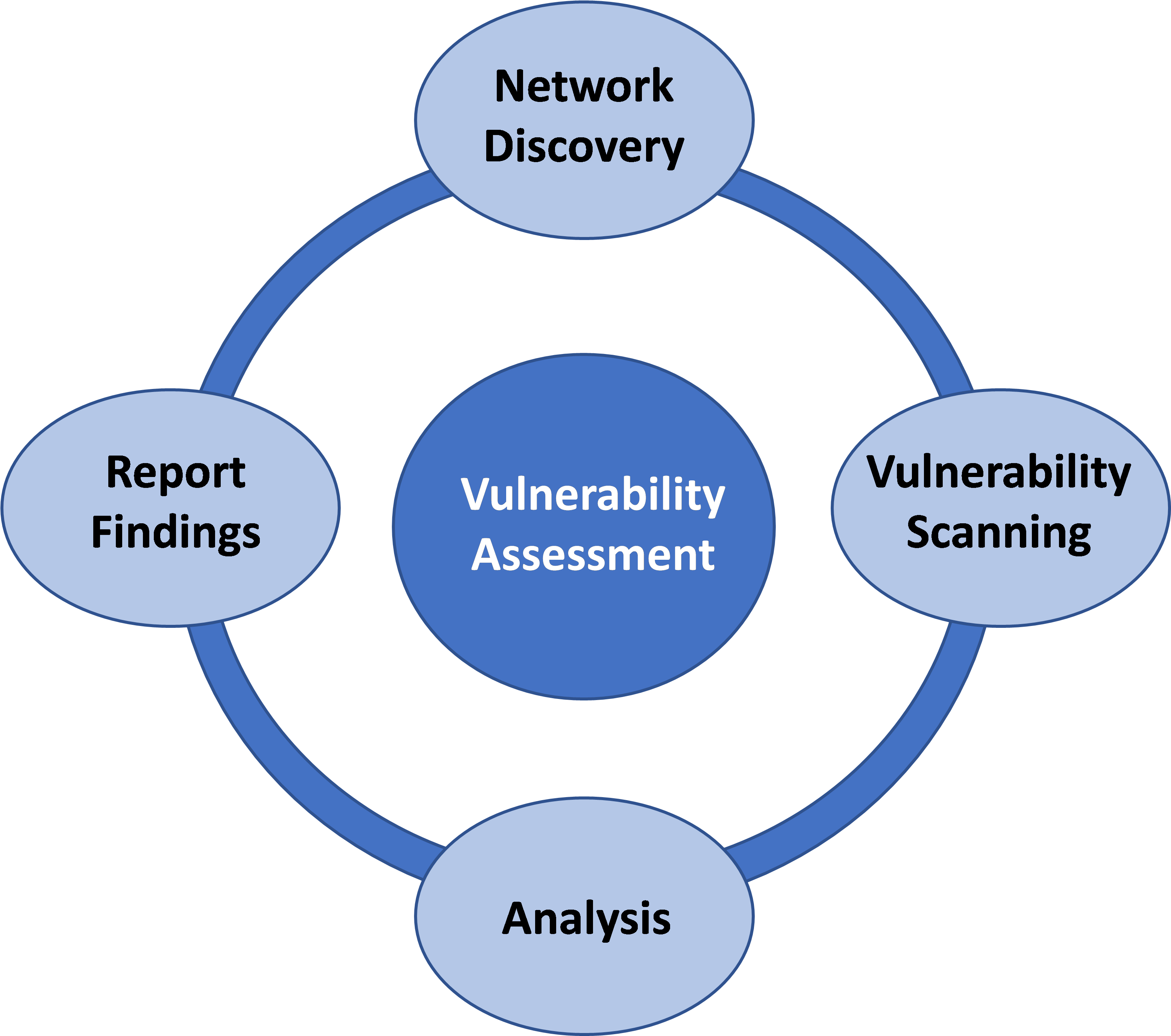
1. Vulnerability Scanning
Vulnerability scanning is the process of using automated tools to identify vulnerabilities in a computer system. Vulnerability scanners typically use a database of known vulnerabilities to compare against a system’s configuration.
- Types of vulnerability scans: There are several different types of vulnerability scans, including:
- Basic vulnerability scans: These scans identify common vulnerabilities in software and operating systems.
- Advanced vulnerability scans: These scans identify more complex vulnerabilities, such as zero-day vulnerabilities.
- Penetration testing: This type of vulnerability test involves simulating an attacker’s actions to identify vulnerabilities that could be exploited to gain unauthorized access to a system.
2. Penetration Testing
Penetration testing is a type of vulnerability test that involves simulating an attacker’s actions to identify vulnerabilities that could be exploited to gain unauthorized access to a system. Penetration testers use a variety of techniques to identify vulnerabilities, including:
- Social engineering: This technique involves tricking users into revealing sensitive information or performing actions that could compromise security.
- Phishing: This technique involves sending fraudulent emails or text messages that appear to be from legitimate sources in order to trick users into clicking on malicious links or attachments.
- Malware: This technique involves using malicious software to infect a system and gain unauthorized access.
3. Security Assessment
A security assessment is a comprehensive evaluation of an organization’s security posture. Security assessments typically include vulnerability testing, penetration testing, and a review of security policies and procedures.
- Benefits of security assessments: Security assessments can help organizations identify and remediate vulnerabilities, improve their security posture, and ensure compliance with regulatory requirements.
- Types of security assessments: There are several different types of security assessments, including:
- Network security assessments: These assessments evaluate the security of an organization’s network infrastructure.
- Application security assessments: These assessments evaluate the security of an organization’s applications.
- Cloud security assessments: These assessments evaluate the security of an organization’s cloud computing environment.
4. Risk Management
Risk management is the process of identifying, assessing, and managing risks to an organization’s security. Risk management is an important part of vulnerability testing because it helps organizations prioritize vulnerabilities and allocate resources to remediate the most critical vulnerabilities.
- Steps in risk management: The risk management process typically involves the following steps:
- Identify risks: The first step is to identify the risks to an organization’s security.
- Assess risks: The next step is to assess the likelihood and impact of each risk.
- Manage risks: The final step is to develop and implement strategies to manage risks.
5. Compliance
Compliance is the process of adhering to laws, regulations, and industry standards. Compliance is important for organizations because it helps them avoid legal penalties and protect their reputation.
- Types of compliance: There are several different types of compliance, including:
- PCI DSS compliance: This compliance standard is designed to protect the security of payment card data.
- HIPAA compliance: This compliance standard is designed to protect the privacy and security of health information.
- ISO 27001 compliance: This compliance standard is designed to help organizations manage their information security risks.
Conclusion
Vulnerability testing is a critical part of any cybersecurity strategy. By identifying and remediating vulnerabilities, organizations can reduce their risk of being compromised by attackers. There are several leading providers of vulnerability testing services in Malaysia. These providers offer a range of services, from basic vulnerability scans to comprehensive penetration testing. By choosing the right provider, organizations can ensure that their systems are secure and compliant with regulatory requirements.
Keyword Tags
- Vulnerability testing
- Penetration testing
- Security assessment
- Risk management
- Compliance
