[Vulnerability Assessment]
Executive Summary
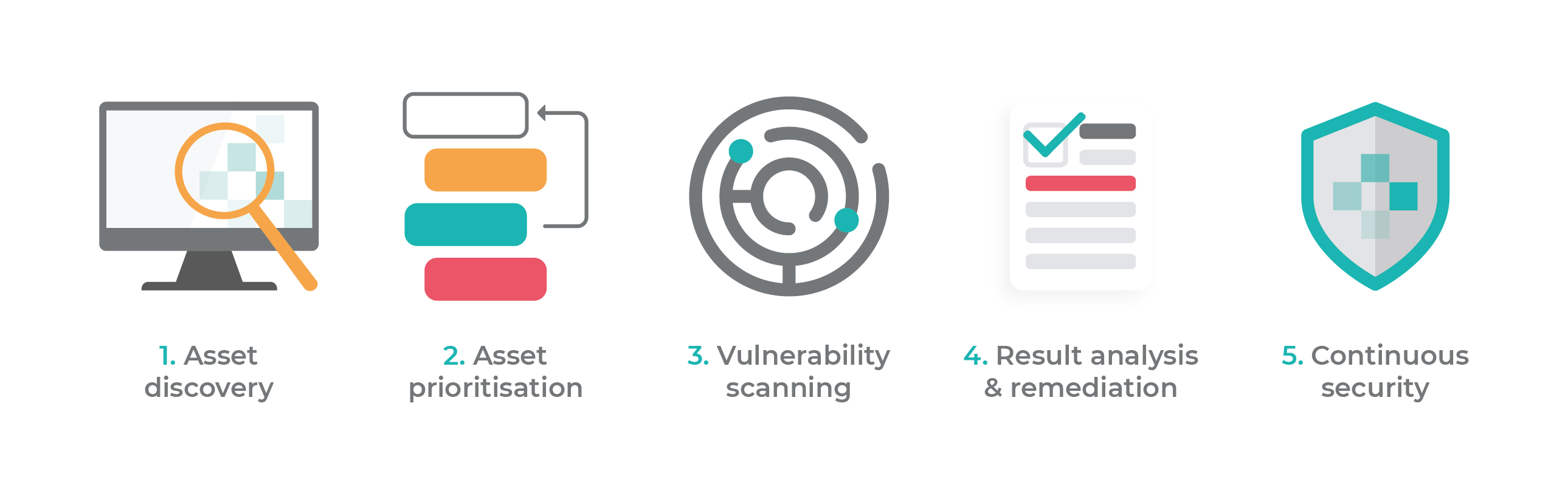
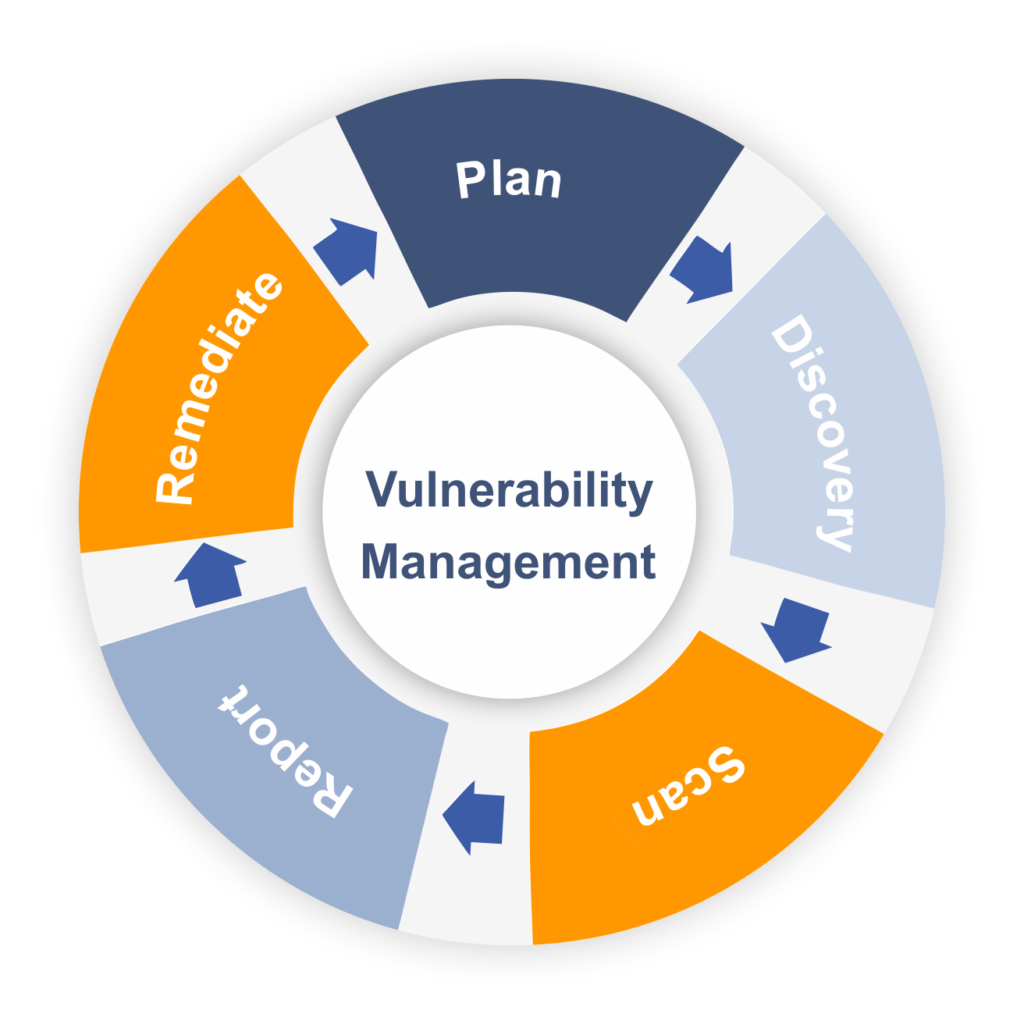
A vulnerability assessment is a comprehensive examination of an organization’s IT infrastructure to identify, catalog, and prioritize security vulnerabilities. This in-depth analysis helps organizations understand their exposure to potential cyber threats and take proactive measures to mitigate risks. Vulnerability assessments play a critical role in safeguarding data, systems, and reputation by empowering organizations to proactively address vulnerabilities before they can be exploited by malicious actors.

Introduction
In today’s rapidly evolving digital landscape, organizations face increasing threats from cybercriminals and malicious actors. A vulnerability assessment is indispensable in safeguarding an organization from these threats. By comprehensively evaluating an organization’s security posture, vulnerabilities can be identified and prioritized, empowering the organization to take appropriate measures to mitigate risks and bolster its overall security.
FAQs
Q: What is the difference between a vulnerability assessment and a penetration test?
- A: Vulnerability assessment identifies vulnerabilities using automated tools, while penetration testing involves simulating a real attack by manually testing vulnerabilities.
Q: How often should vulnerability assessments be conducted?
- A: Regular assessments are crucial to keep pace with evolving threats, typically conducted quarterly or semi-annually to ensure timely identification of emerging vulnerabilities.
Q: Who should conduct a vulnerability assessment?
- A: Internal IT teams or external security experts can conduct vulnerability assessments. External experts provide an independent perspective and advanced tools.
Top 5 Subtopics
1. Vulnerability Scanning
- Automated tools scan networks and systems for known vulnerabilities.
- Identifies and classifies vulnerabilities by severity.
- Provides an overview of vulnerabilities to prioritize mitigation efforts.
2. Penetration Testing
- Simulates real-world cyberattacks to assess vulnerabilities’ exploitability.
- Uncovers vulnerabilities that automated scans may miss.
- Validates the effectiveness of implemented security controls.
3. Security Configuration Assessment
- Examines the configuration of operating systems, applications, and network devices.
- Identifies deviations from recommended security configurations that create vulnerabilities.
- Ensures that security measures are implemented correctly and effectively.
4. Code Review
- Analyzes application code to identify security vulnerabilities.
- Detects vulnerabilities such as buffer overflows, XSS, and SQL injections.
- Uncovers vulnerabilities that traditional scanning tools may miss.
5. Social Engineering Assessment
- Evaluates an organization’s susceptibility to social engineering attacks.
- Tests employees’ ability to recognize and respond to phishing emails, smishing, and other social engineering tactics.
- Raises awareness and strengthens defenses against social engineering threats.
Conclusion
Vulnerability assessments empower organizations to understand their security posture and proactively manage risks. By identifying and prioritizing vulnerabilities, organizations can strategically allocate resources to address the most critical threats. Regular vulnerability assessments, coupled with effective mitigation measures, enable organizations to maintain a strong security posture, protect valuable assets, and maintain business continuity in the face of evolving cyber threats.
Keyword Tags
- Vulnerability Assessment
- IT Infrastructure Security
- Cybersecurity
- Risk Mitigation
- Penetration Testing
